Waste Hierarchy- The Inverted Pyramid
Waste Hierarchy- The Inverted Pyramid
What is the Inverted Pyramid?
The inverted pyramid that shows the most important areas of sustainability at the top, with the least important at the bottom. The hierarchy allows us analyse our relationship with waste and how we can effectively tackle the battle in a sustainable way.
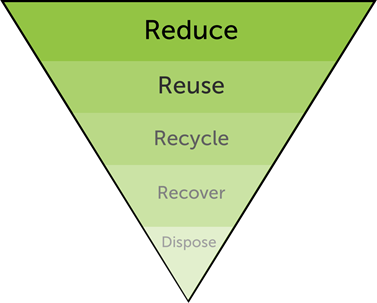
This pyramid is used to show how we tackle waste, as shown in the diagram above, Reduce is the most crucial way to tackle the global waste problem. In contrast at the bottom of the pyramid we have Dispose which is the least productive way to fight waste. By disposing of waste without much thought it can cause more harm than good as there are certain goods that need to be disposed of correctly, if not they can be harmful to the environment.
Components of the Inverted Pyramid
Let’s take a look into the key components of the pyramid in more detail to gain a better understanding of how this approach will tackle the fight against waste.
Reduce
The concept of Reduce is to reduce the amount of non-sustainable materials used in products by finding alternatives. For example, using paper bags instead of plastic bags and finding “green” alternatives to key materials used to create products.
Reuse
Reuse means using second- and rather than going straight to new items. An example is buying second-hand clothing instead of new, by doing this you are using products that have already been manufactured. By re-using items, it allows for be less wastage forced out into the environment as well as it being a cheaper alternative in the majority of cases
Recycle
Recycling is turning old products into something brand new. In our sector, it means taking the metals out of your mobile phones so that they can be used for making new products. There is a slight downfall to this as this component does use a lot of energy which is why Reuse is the preferred option.
Recover
Recover is associated with energy recovery. It means turning waste into energy such as burning biomass to create heat. This is something Re-Tek stand by as we have a Biomass Boiler which heats the whole facility. As well as making the use of solar panels to create energy to power the facility.
Dispose
The last area that we want to avoid at all costs, disposal means putting waste into the ground in landfill. It should only occur when all other options have been exhausted and there is no other way.
Waste Hierarchy and the Circular Economy
The two go hand in hand as they are both models that have the outcome to be beneficial to our environment. They both have the objective to reduce the overall waste output. The Circular Economy has the main goal to extend a product’s lifecycle, and to keep it in the economy for longer. This is done by finding alternatives to immediate dispose after it is no longer needed by someone or a business.
The diagram below shows the difference between how the Linear Economy model compares to the Circular Economy model.
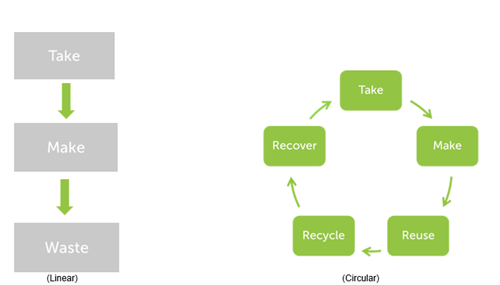
As a society, we currently, generally operate within the Linear Economy, we are trying to move towards the Circular Economy as a whole, as we are realising the positive potential it has in some aspect of the supply chain throughout all industries.
Recent News
Waste Hierarchy- The Inverted Pyramid
January 11, 2022
Even More Awards for Re-Tek
November 24, 2021
Local MSP visits Award-Winning IT Disposal Company
October 25, 2021
Even More Awards for Re-Tek
Even More Awards for Re-Tek
Re-Tek (UK) Ltd are thrilled to share that we have been awarded a 4-star rating at the Zero Waste Awards 2021.
Why Re-Tek was Awarded a 4 Star Rating
Re-Tek was awarded 4 stars due to the conscious efforts of our reuse rate of equipment throughout the facility which reduces our overall wastage output. Cardboard boxes are reused by our despatch team to limit our reliance on energy-intensive cardboard recycling, and our office equipment is second hand to stop equipment needlessly being recycled. Used coffee grounds are used by employees to fertilise home gardens and our employees are encouraged to separate their personal waste.
An element that stood out to the judging panel was our 83% re-use rate on all devices with the remaining 17% being recycled in line with the WEEE directive.
The Award Ceremony
The Award Luncheon was held on Friday 19th November at the Skyloft, Millbank Tower in Central London which was hosted by LetsRecycle.com.
This event allowed us to network with companies who operate within different industries, as well as learning processes businesses are taking to tackle the the issue of waste locally and globally.
Keynote speaker Anna Willetts, Senior Vice President of CIWM gave her perspective on the issue of Waste which gave a different insight to the topic.
Looking to the Future
With the recognition of this rating, we are continuously looking at our practices to identify how we can be even more sustainably efficient internally as well as externally. As a company we already working on ways on how we can achieve a 5-star rating in the future.
Even More Awards for Re-Tek
This Award is the second award received by Re-Tek in under 2 months. In September we won “The Best Circular Economy Company” at the CRN Awards.
These awards are attributes to Re-Tek’s commitment to the Circular Economy and extending the life of electrical products in an sustainable way.
Re-Tek is constantly seeking ways to improve daily operations to ensure we are providing the best service we possibly can to our customers, which we will continue to do throughout our practices.
Recent News
Waste Hierarchy- The Inverted Pyramid
January 11, 2022
Even More Awards for Re-Tek
November 24, 2021
Local MSP visits Award-Winning IT Disposal Company
October 25, 2021
Local MSP visits Award-Winning IT Disposal Company
Local MSP visits Award-Winning IT Disposal Company
Re-Tek (UK) welcome Collette Stevenson, MSP for East Kilbride, to their state of the art IT disposal facility.
Showcasing East Kilbride Business
Re-Tek (UK) Ltd are a growing business in the East Kilbride community. Situated in the Kelvin South Business Park, Re-Tek are a member of a strong business network in the area. As supporters of South Lanarkshire’s ‘Routes to Work’ programme, Re-Tek have provided employment for the long-term unemployed in East Kilbride. Re-Tek’s Managing Director, Gordon Lowrie, spoke with Collette about Re-Tek’s focus on good working conditions and local recruitment.
A Tour of the Facility
Ms. Stevenson was given a tour of Re-Tek’s facility by Gordon Lowrie, the managing director. The visit took place on Wednesday the 20th October, just two weeks before the start of COP26. The tour highlighted Re-Tek’s continued investments in renewables and energy efficiency. Additionally, Re-Tek were able to showcase their custom-built volume build centre, which has allowed to business to expand their service offering. Re-Tek’s project director, William McPherson, explained Re-Tek’s ‘cradle-to-grave’ model, which allows the business to sustainably handle IT equipment throughout from deployment to disposal.
“We were delighted to welcome Collette to our facility today. Collette was very engaged with our sustainability messaging and provided us with some useful insights from a government perspective. We were able to have a stimulating conversation around green issues and the best methods for tackling them.” – Gordon Lowrie, Managing Director
Going Over the Government's Green Goals
Ms Stevenson was able to provide some insight into the government’s environmental strategy. The Scottish government has made significant changes to tackle climate change head on. Re-Tek were able to better understand the government’s sustainability goals. Similarly, Re-Tek provided Ms Stevenson with a better understanding of how IT Asset Disposal can help in the fight against climate change.
“It was great to visit Re-Tek and meet Gordon Lowrie and employees who talked through the work they do. Their commitment to renewable energy is impressive, and it was great to see how their operations make a positive impact in the fight against climate change. They’ve gone from strength to strength over the years and I have no doubt their success will continue long into the future.” – Collette Stevenson, MSP East Kilbride
Anticipation Builds for COP26
Re-Tek extended an invitation to Ms Stevenson for their upcoming sustainability webinar, ‘“Closing the Loop” in ICT’. The event, which takes place during COP26, will discuss the circular economy in the UK economy. Invites have also been sent to Ms Stevenson’s peers on the Net Zero, Energy, and Transport Committee.
Recent News
Waste Hierarchy- The Inverted Pyramid
January 11, 2022
Even More Awards for Re-Tek
November 24, 2021
Local MSP visits Award-Winning IT Disposal Company
October 25, 2021
Re-Tek's Revenue Share Model: How is it calculated?
Re-Tek's Revenue Share Model: How is it calculated?
Looking to dispose of your IT but don't know how much it's worth? Re-Tek will give you an insight into how we calculate how much money you get back.

What is a Revenue Share Model?
A revenue share model allows you to get a cut of the profits that Re-Tek make. Why? Because it is important that you are rewarded for taking the right steps to becoming more sustainable.
Re-Tek are able to provide some financial return on most IT disposals. It all depends on our operating costs and the value of the used IT.
What is the Re-Tek Formula?
Step 1
First, Re-Tek will look through and note everything we have collected from your business. We put this into our bespoke database which creates an asset management form.
Step 2
From there, our re-marketing team will assess the devices including their condition. With over 10 years of experience in the industry, they can tell instantly what has value and what doesn’t. But we don’t work on instinct alone. So, our re-marketing team will check the pricing with our network of buyers to make sure it is correct.
Step 3
Re-Tek then work out the operational costs for the job. This includes transportation costs, working hours, and energy use. This is taken off of the sale value.
Step 4
Then, Re-Tek are able to offer you a financial return on your IT equipment. This will be a 70/30 profit split. From there, you can use your share for whatever you would like. Don’t know what to spend it on? We have a few ideas that businesses like yours are using.
What should I do with the money?
You have several options when you receive your quote. Some businesses decide to use their money themselves while others will donate it to charity. How do you know which is right for your business?
Subsidise your IT Refresh
If you are disposing of redundant IT, you are likely buying new equipment. Use the money generated by your old IT to cover some of that cost. You can therefore lower the lifetime cost of your IT.
Make a Donation to Charity
Does your company have an associated charity or foundation? Re-Tek are able to donate to a charity of your choice. Turn your redundant IT into a force for good. You can use these funds to boost your corporate social responsibility.
Add Funds to Another Budget
Do you have departments crying out for bigger budgets? Give them some extra finances from your waste IT. This could give your marketing an extra boost or could buy some extra equipment for your warehouse team.
Recent News
Waste Hierarchy- The Inverted Pyramid
January 11, 2022
Even More Awards for Re-Tek
November 24, 2021
Local MSP visits Award-Winning IT Disposal Company
October 25, 2021
What is Digital Agility? 3 Key Benefits to a Digital Transformation Strategy for your Business
What is Digital Agility? 3 Key Benefits to a Digital Transformation Strategy for your Business
What is Digital Agility?
Digital Agility is all about adaptability. It requires businesses to quickly update or change their processes when they need to. It requires consideration of every part of the IT function, including hardware and software.
Sometimes known as Digital Transformation, Digital Agility pushes for digital innovation. It forces companies to evolve their digital strategies to reach desired outcomes.
Growing Trend or Fruitless Fad?
Like all new business strategies, digital agility has its supporters and its critics. Whether you are for or against it, the International Data Corporation (IDC) think it is here to stay. Their forecasts show digital agility spending reaching $1.97 trillion in 2022. This is an annual increase in spending of 16.7 percent from 2017 to 2022.

What are the Benefits of Digital Agility?
Having read about digital agility, you may be wondering “why should I care about this?”. There are several key benefits to digital transformation.
Increase your Adaptability
Your business can benefit from being more capable of adapting to market changes. A digital agility strategy means that most of the hard work is already done. That means that you can react swiftly to market changes. This helps keep your business running smoothly for your employees and customers.
A Boost to your Competitive Advantage
Innovation is key to building sustainable competitive advantage. Digital transformation can therefore be an asset for your company. Putting in place these processes has been shown to improve productivity, profitability, and to reduce costs. Embracing change can be the difference between leading your market and falling behind your competition.
Streamline your Processes
Digital transformation uses automation to review and clean data. You can then bring together data in an easy to access and organised way. This makes it easy to identify market trends and areas for improvement.

How do I become Digitally Agile?
Now that you know the benefits of digital transformation, you might be wondering where to start with it.
Below are a list of the key considerations for those moving towards a digitally agile way of working.
Drive Home a Digital Culture
Embedding a digital culture is the first hurdle that you will need to overcome. Convincing senior managers of the benefits of digital transformation isn’t easy. Then, you need to secure company buy-in. Otherwise, your digital strategy will likely fail at the first big market change.
This also means embracing change so that you are ready to adapt to, or even capitalise on, market changes.
Building the Right Processes
Advanced analytics and cognitive computing are just two ways that data can be used to drive business decisions. Setting up these processes takes time at first, but will save time when key decisions need to be made.
Keep your Data Clean
Reviewing the quality of your data is essential when becoming digitally agile. This means removing any incomplete or corrupted data. Failing to do this could mean you make bad decisions following large market changes. It is therefore important to set up some automation to consistently review data and sort inconsistencies
How has Covid-19 affected Digital Agility
The pandemic has forced businesses to reconsider how they make decisions. The sheer amount of change needed in a short period of time put the spotlight on digital transformation. Never before had companies of all sizes felt so much pressure to make their business models fit changing requirements.
55% of companies say the pandemic has resulted in permanent changes to their organisational strategy.
Changing Market Landscape
Businesses have already made changes to their strategy. Sixty percent of businesses say that Covid-19 has forced them to adapt their change management processes. Cloud-based activities have also seen a large uptake, with 64% of businesses making these changes. We’re living during a time that demands rapid change, quick launches, and innovative solutions, and many companies have already taken the first steps to achieve this.
How can IT Asset Disposal help with Digital Agility
IT Asset Disposal should be a key consideration for your business when moving towards a digitally agile strategy. IT Asset Disposal can ensure that you can make IT changes faster. It will allow your company to recover some of the value from redundant IT.
Changing IT Requirements
Digital transformation means new technological and software needs. That also means that your IT suite will need to change too. IT asset disposal can help return some of the value from your old IT assets when you need to upgrade your equipment.
Re-Tek Continue Pioneering the Circular Economy with Momentous Award Win
Re-Tek Continue Pioneering the Circular Economy with Momentous Award Win
Re-Tek UK are proud to share that we have won the inaugural “Best Circular Economy Company” award at the CRN UK Tech Impact Awards.
A Big Night For Sustainable IT
Thursday the 16th September saw many of the IT channel’s most sustainable businesses come together for the inaugural Tech Impact Awards. Run by CRN, these awards celebrated the efforts of IT channel partners becoming more environmentally friendly.
Re-Tek the Night's Biggest Winners
There was stiff competition for the “Best Circular Economy Company” Award, with industry giants HP and Computacenter both nominated. However, Re-Tek pulled off the upset by picking up the award. In a category of 14 strong competitors, Re-Tek were delighted to come out on top.
Why did Re-Tek win "Best Circular Economy Company"?
Re-Tek’s continued efforts to develop and drive forward the circular economy have resulted in the receipt of this award. Judges were impressed by Re-Tek’s commitment to renewable power which allows the business to offset the carbon emissions of their customers. Re-Tek’s innovative processes for extracting critical raw materials was more important however. Re-Tek have taken steps towards saving key materials such as gold, cobalt, and tantalum.
“A huge congratulations and thanks goes out to all of our team for their hard work and dedication in helping us become a leading and trusted partner, pioneering the Circular Economy and driving the industry forwards.” – Gordon Lowrie, Managing Director
What's Next for Re-Tek following this award?
Re-Tek will continue to offer best in class re-manufacturing and re-use services to our customers. We are innovating our processes to ensure that we offer cost-effective and secure IT lifecycle services to our partners. Re-Tek are committed to lowering our carbon footprint, and we are looking into new ways to achieve net carbon zero.
“The accelerating worldwide focus on carbon reduction means that the likelihood of many of these recognised initiatives will become an expected standard in our industry in the future where we will continue to invest in progressing and disrupting standard practice therefore reducing the impact technology has on our environment” – Kevin Culligan, Chairman and Co-Founder.
Recent News
Waste Hierarchy- The Inverted Pyramid
January 11, 2022
Even More Awards for Re-Tek
November 24, 2021
Local MSP visits Award-Winning IT Disposal Company
October 25, 2021
How much Carbon does your IT really emit? A Brief Explanation of Embodied Carbon
How much Carbon does your IT really emit? A Brief Explanation of Embodied Carbon.
The embodied carbon of your electronic equipment is the sum total of the energy required to manufacture a product. You can better understand the full environmental impact of your purchases by understanding this. Below, you can find out how embodied carbon can be calculated and what it means for the environment.

A Lifetime of Carbon Emissions
When talking about the environmental impact of our daily commute, we only talk about the carbon emitted from our car’s exhaust pipe. Likewise, we talk about how the switch to electric cars would reduce the carbon emissions from our commute. However, this only takes into account the operational carbon emissions from the fuel used to power our cars. We don’t consider the carbon emissions from the manufacturing plants for both types of car. And what about the energy needed to mine and refine the raw materials? This is what we call embodied carbon. This can alter the way we think about the environmental impact of our purchases.
What is Embodied Carbon?
Embodied Carbon, sometimes known as Embedded Carbon, is a calculation of the carbon emissions from the manufacturing process. Ultimately, this means that there are other factors to the carbon emissions that come from your purchases. For example, the amount of tantalum required for 1,000 printed circuit boards creates 301.6kg of greenhouse gases (CO2-eq). Each of these printed circuit boards would be used in a PC, which adds to the carbon footprint of the final product. Therefore, the full environmental impact of your PC goes beyond its energy use. If you sum together the footprint of each component, you will have the material footprint of one PC. Multiply this out for a suite of 2,000 PCs and laptops and you can begin the see the full impact of your IT suite on the environment. Is there a way to limit this environmental impact?
How we can Harness Embodied Carbon
Once a PC or laptop has been manufactured and distributed, the majority of its carbon footprint has already been accounted for. This is the energy from the material mining, the manufacturing process, and the delivery to your facility. You begin to add to that material footprint through the energy required to run them. Many companies have realised that they can lower their operational carbon emissions by making some key changes. These changes include using renewable energy or switching machines off when not in use.
However, you can still make the most of the energy used to manufacture the product. You can do this by re-using the product itself or any of its composite parts. This gives these materials a second lease of life and reduces the material footprint of new products. Additionally, using second-hand IT lowers the material footprint of your IT estate as these products have an extended lifetime.
Calculating the Embodied Carbon of your IT
Calculating the total embodied carbon of a PC or laptop is not easy. Due to the number of different materials and components in these devices, keeping track of the carbon emissions for everything can be tricky. Therefore, getting the most accurate result would require a database of each different element with their specific carbon footprint. However, this would be very difficult to achieve. Alternatively, manufacturers will provide a breakdown of the key carbon footprint of each aspect of a PC. For example, the table below shows the values for a Dell Optilex 7760 All-in-One Desktop:
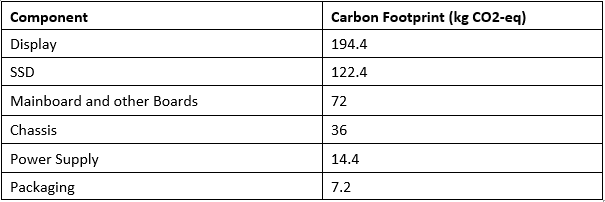
From this, you can calculate that the Dell Optilex 7760 All-in-One has an embodied carbon of 446.4kg CO2-eq. Over the course of a typical 4-year lifecycle, this accounts for around 62% of the total carbon footprint of the product with the remainder coming from the use of the product. Carbon footprint assessments for other Dell products can be found here.
A Little Perspective
200 Dell Optilex 7760s would create the same amount of carbon emissions as a full Boeing-747 travelling from London to New York over a 4-year lifetime.
Improving the Carbon Footprint of your IT
With this knowledge of the material footprint of your IT, you can begin to lower the environmental impact of your IT estate. Firstly, by extending the use period of these devices you could lower the overall impact of a PC or laptop. This is because over half of the carbon footprint of a device comes from the initial manufacturing rather than the use. This means that switching to renewable energy only tackles a small proportion of the problem. Extending the lifecycle of these PCs would flip this on its head. Using a PC over a period of 8 years would cause approximately 1,000 kg CO2-eq compared to using a PC over 4 years causing 720 kg CO2-eq.
A Better Way to Track the Material Footprint
Keeping track of the carbon footprint of a device over its lifetime remains difficult. This is particularly true when the product has been repaired using new components. Introducing a Digital Product Passport could be the solution to this problem. This would create a centralised bank of information for each device. This information would include the carbon footprint of each component within the device. By using this technology, you would be able to understand the full extent of the embodied carbon in your devices at the touch of a button.
The Material Footprint of your e-waste
The Material Footprint of your e-waste
Understanding the environmental impact of the products that we buy is a key consideration in our current environmentally conscious world. We care more now about the impact that our buying behaviours have on the Earth. Whether it’s choosing products in recycled packaging or buying organic vegetables, knowing the impact of our supermarket purchases is fairly easy. But how do we know the environmental effects of our electronic equipment?
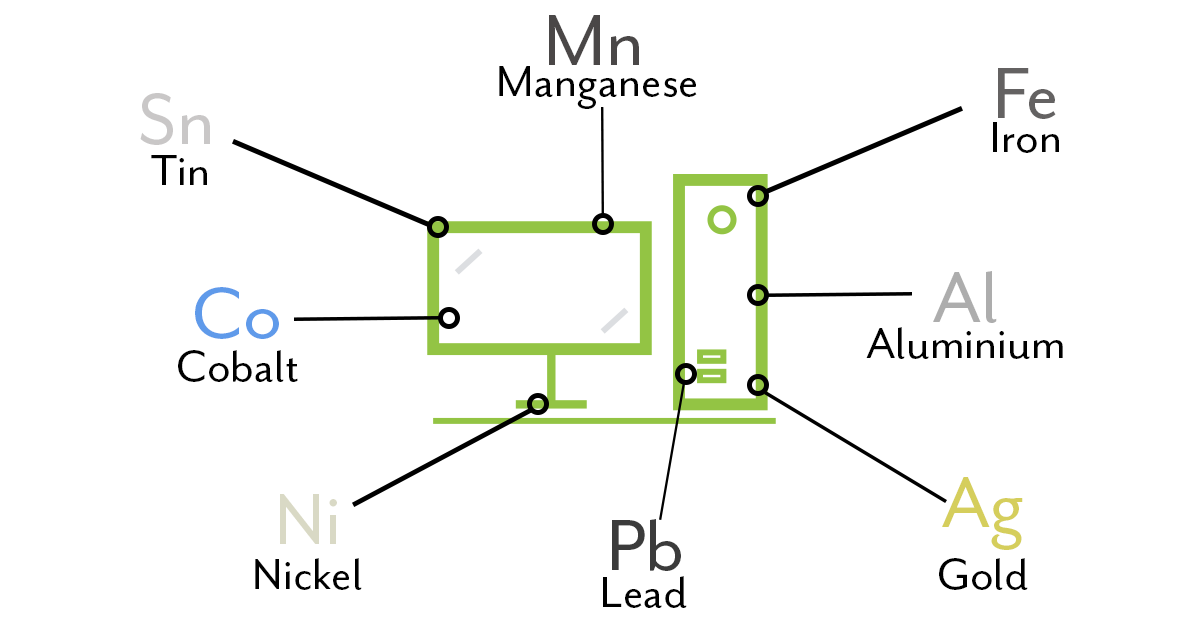
Material Footprint: The anatomy of your IT
A product’s material footprint is an indicator of its lifetime carbon footprint. It allows you to consider all of the carbon emissions required for the production and use of your products. For example, the material footprint of a car takes into account not only the fuel consumption of the car itself, but also the carbon footprint of the raw materials required in its production. This includes the carbon emissions from the mining of the iron ore and from the steel production factory among other factors. Ultimately, it is an indicator of the strain put on the environment throughout the lifecycle of the product.
Why is the Material Footprint Important?
Knowing the environmental impact of your buying behaviour is no use if you can’t make improvements. By understanding how your IT is produced, you can take the necessary steps to lower your material footprint. You have several options to improve your own material footprint with regards to your IT.
Reduce your carbon emissions
The first way to lower the material footprint of your IT devices is to limit the carbon emissions from their operation. This means making the switch from non-renewable energy to renewable energy. This switch limits the material footprint of your IT over its lifetime at your company.
Purchase low polluting products
The second option is to purchase products that have little impact on the environment in their production. This means selecting products which use recycled raw materials, or which have lower specs and thus lesser material requirements. This helps limit the environmental impact of the raw materials needed.
Re-use and Re-manufacturing
The final and easiest option is to extend the lifecycle of your IT. This means that your IT can stay on the market for twice or even three times as long as it would normally. Using second-hand IT instead of new IT reduces the strain on raw material production.
Global Material Footprint Statistics
The total global material footprint rose from 43 billion tonnes in 1990 to 92 billion tonnes in 2017 – an increase of 113%. This highlights our increased reliance on raw materials in recent years. This is expected to grow to 190 billion tonnes by 2060 if there is no rigorous political action taken.
What is e-waste?
E-waste or electronic waste is created when an electronic product is discarded after the end of its working lifecycle. The term e-waste covers almost anything that is powered by electricity. This includes PCs, laptops, smartphones, cameras among others.
It is important to make a distinction between e-waste and everyday waste. E-waste can be particularly dangerous due to the toxic chemicals used in their production. This can lead to these hazardous metals leaking when they are sent to landfill.
What the Material Footprint means for e-waste
Our consumption of electronics is increasing while product lifecycles shorten, leaving a mountain of e-waste in our wake. E-waste is now the fastest growing waste stream worldwide, increasing by 38% since 2010.
This means that our material footprint is increasing as we continue to purchase new products which use critical raw materials such as tantalum and cobalt. Mining these raw materials causes a huge amount of pollution.
Limiting Your Impact
Research has shown that UK households and businesses produce 1.45 million tonnes of electrical waste each year. The e-waste research organisation Material Focus calculates that at least 500,000 tonnes of the waste were thrown away, stolen, or hoarded. Its latest study suggests un-recycled household electricals cost the UK over £370m a year in lost materials like gold, copper, aluminium, and steel.
By re-using these critical materials, through recycling and re-use, you can limit the carbon footprint of your IT estate. Specialist e-waste disposal companies are able to give these materials a second lease of life on the market. This lowers the lifetime material footprint of your IT. Other steps to limit your impact include:
- Try not to update your electronic equipment with every new release, wait until your electronics are reaching the end of their life cycle before replacing them.
- Repair your items before resorting to discarding of them straight away.
- Donate or sell your items if they are still in working condition to extend their life.
Why is it Important to Recycle e-waste?
It is important to recycle and discard of your e-waste in the correct format as most electronic products contain some form of toxic materials such as mercury and lead. These materials can negatively affect the environment. Also, this can cause high levels of air, soil, and water pollution.
Companies are constantly seeking to reduce the amount of waste they send to landfill. Policies which tackle e-waste specifically stop e-waste from being dumped in landfill where toxic materials can spread into the soil. Eventually, these traces of toxic materials pool into the ground below the landfill which has severe environmental consequences.
The more E-waste and metals that resort to landfill the higher the trace of these toxic materials will show up in the groundwater.
How Re-Tek are Combating the e-waste Crisis
Re-Tek was founded on the core principles of the circular economy and at the heart of our processes is the desire to extend the lifecycle of all products that we process.
Re-Tek actively work to get as much value as possible from each item of equipment. Ensuring to get the most from an item is critical for the environment and extends the lifecycle ICT through repair, refurbishment, and reuse activities. If we cannot repair an item, or it is not economical to do so, functional parts are harvested before being responsibly recycled.
Re-Tek aims to be a zero waste to landfill company. This is being carried out by ensuring re-use of equipment. Re-Tek diverted approximately 700 tonnes of equipment from both landfill and recycling (markets) in 2017, which equates to a significantly reduced environmental impact.
Finally, Re-Tek have been recognised for our best practice in the industry – achieving the “Remade in Scotland” award from Made in Scotland and the “Sustainability” award from CeeD Scotland.
Choosing an ITAD: 6 Tips to Help you Make the Right Choice
6 Tips for Choosing the Right ITAD Partner
Are you upgrading your IT and thinking “what do I do with my old IT equipment”? Or do you have old IT taking up valuable space as you move back into the office? A quick Google search will produce a long list of IT Asset Disposal (ITAD) companies ready to take control of your end-of-life IT. But how do you know which of them to trust? What makes one ITAD better than another?
Your IT holds valuable, confidential information about your business, your employees, and your customers. Ensuring that it is disposed of through the right channels is vital. Keeping your data secure is essential and failure to do so can have some severe consequences. That makes choosing the right partner to dispose of your old IT a difficult choice. Make sure that you are making an informed choice by following these simple steps.
What is an ITAD?
Before we dive into picking an ITAD partner, we need to know what an ITAD is. ITAD stands for Information Technology Asset Disposal. Simply put, ITAD is the process of disposing of your IT equipment in a secure and environmentally safe way. While you may have processes in place to protect your data on your servers, it is just as important to protect your end-of-life assets. Therefore, ITAD firms are the final line of defence for your IT equipment and your cybersecurity.
ITAD companies have several processes for disposing of your IT assets. ITAD firms provide solutions for hard drive shredding, recycling in line with the WEEE directive, and secure data erasure, helping businesses when they upgrade their IT suite by providing a secure channel to dispose of their IT.
When choosing to trust a new partner to manage your IT Assets and Confidential Data, you face a dilemma. How do you know you’re making the right decision? What criteria, industry guidance or performance measures do you work from, to ensure your decision is solid?
Tips for what to look out for when choosing an ITAD partner are:
- Accreditations
- Expertise
- Price
- Environmental Policy
- Traceability and Transparency
- Security Practices
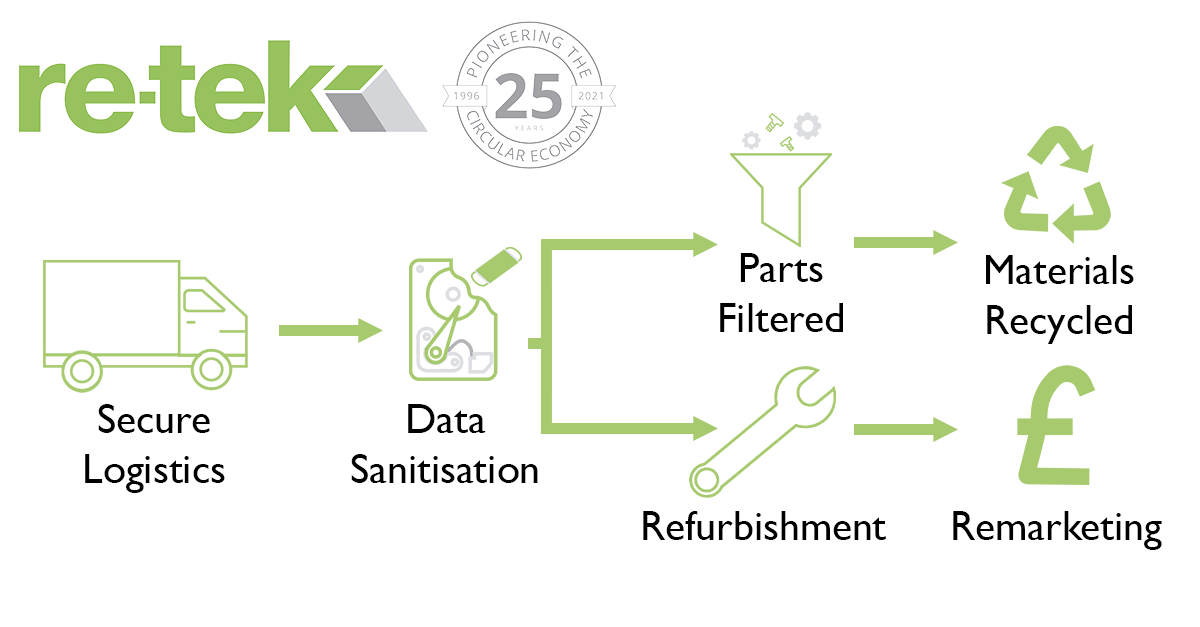
Tips for Finding the Right IT Disposal Partner
Before we dive into picking an ITAD partner, we need to know what it is. ITAD stands for Information Technology Asset Disposal. Simply put, ITAD is the process of disposing of your IT equipment in a secure and environmentally safe way. ITAD firms will take your end-of-life IT and ensure that it is safely disposed of.
ITAD companies have several processes for disposing of your IT assets. ITAD firms provide solutions for hard drive shredding, recycling in line with the WEEE directive, and secure data erasure. ITAD companies help businesses when they upgrade their IT suite by providing a secure channel to dispose of their IT.
Accreditation
One of the first things that you want to know about an ITAD partner is if they have the relevant accreditations. These accreditations mean that the ITAD firm has been audited and vetted to meet industry standards set by experts.
Here is a list of some of the key accreditations to look out for:
- ISO 9001 – setting out the criteria for a quality management system. This includes a focus on the customer and internal audit processes for continual improvement.
- ISO 27001 – this standard sets out the processes for managing information security. As disposal companies deal with your confidential data, it is essential that they have this accreditation.
- Blancco partner – Blancco is the market-leading data erasure software and is approved by the National Cyber Security Centre. Ensure that your ITAD partner is using this best-in-class software.
These accreditations give you peace of mind that your partner is up to the highest standard. Make sure that these are still up to date and are visible on their website to give yourself peace of mind that you are working with an expert.
Expertise
On top of having all the relevant certifications, you can trust an ITAD firm that has years of expertise under their belt. Companies with a long history in the industry will have better connections for reselling your IT equipment, more efficient processes for collecting and disposing of your IT and have a superior understanding of your needs. Remember, there is a reason that these companies have been around for so long. You should be aware of the company’s track record, if there is any uncertainty you should avoid these companies. Moreover, you should ensure that your ITAD partner can provide you with certifications on the topics of erasure and recycling electronic devices securely.
Governmental regulations are constantly changing, so make sure you are working with an ITAD that has a strong knowledge of the market and who remains aware of these changes as they happen.
Price and Financial Rebate
Make sure that you unlock the value in your end-of-life IT. Most of your IT equipment will have re-sale value in the secondary market. Any ITAD firm worth their weight will have a financial rebate policy whereby they will return some of their profit back to you.
Additionally, some firms will offer you the opportunity to donate your old IT equipment to a charity or organisation of your choice. These services allow you to improve your corporate social responsibility practices using assets you already own. Building your corporate image can become even easier as ITADs take care of every step, from collection of your assets, to delivering them to the organisation of your choice.
Zero Waste to Landfill
Environmental reporting is one of the most important aspects of modern business. Working with a partner that understands the importance of this is therefore essential. Choose an ITAD company that follows a zero-landfill policy. This gives you peace of mind that your waste IT has been recycled properly in line with the WEEE directive.
Transparency
To guarantee that your IT is being handled as you expect it to be, make sure that your ITAD partner is transparent about their practices. This means making sure that you have access to a suite of reporting to follow the full chain-of-custody of your data-bearing assets.
Security Practices
Ensuring that every step throughout the ITAD process is fully documented with certificates for both the destruction and wiping of drives helps to maintain security throughout your supply chain. Be aware of the software being used by your ITAD. The company should be using highly credible software such as the world leading Blancco overwriting software.
Remember that your end-of-life IT houses valuable data for your business. Therefore, you should choose a partner that follows strict security practices throughout the process. This could include having unmarked, GPS-tracked vehicles that collect your assets to ensure they are safe at all times. It could also include having secure holding facilities for your assets prior to the data wiping process. Think about what level of security you expect with your current IT assets and make sure that your ITAD partner aligns with those standards.
Why is it important to get it right?
It is important to choose the right ITAD partner for your company as you do not want any of your secure data to get leaked or not processed in the correct format. You want to be confident that your ITAD partner can provide you with the exact processes and audit trails that your equipment has went through until the end process e.g., re-used, recycled etc.
If your data is not disposed of through the proper channels, it could cost you £17.5 million or 4% of your annual turnover. Not to mention that your reputation as a credible brand could be tarnished following one of these incidents. Ensuring that your data is disposed of correctly is key to keeping your business safe.
Why choose Re-Tek?
At Re-Tek Limited we provide a wide portfolio of offerings to our customers. As previously stated, we have all of the main, important accreditations that allow us to do our work securely and effectively, which is GDPR aligning. Services that we offer include:
- Secure data erasure
- IT asset re-sale and reporting
- WEEE Recycling, which is wiped to NCSC standards
- Secure Shredding
- Decommissioning
5 Tips for Keeping your Data Secure
5 Tips for Keeping your Data Secure
Step 1: Ensure that your data is kept under lock and key
Strong Passwords Make Strong Defences
The key to keeping your data safe is making sure that it does not fall into the wrong hands. A strong password is the first step when it comes to stopping people from stealing your confidential information. If your password is not strong enough, hackers can easily get into your system to steal your personal data. Make sure that your passwords are changed regularly to keep your systems safe.
How do hackers get into your system?
There are several methods that hackers will use to try and access your system. Understanding these methods will help you to protect against them. This will give you an insight into what the main threats are to your cyber security.
- Brute Force Attacking – Hackers will try to crack your password by guessing. They will therefore try generic passwords first to try and gain access to your system. Examples of generic passwords include ‘Password1’ or passwords that contain personal information, such as your name or your company. Most of these attacks use automated processes to attempt different combinations of words and numbers. Ensure that your passwords are difficult to guess to keep your data safe.
- Dictionary Attack – This is very similar to a brute force attack as hackers will try to guess your password. However, instead of trying common passwords, they try a much larger selection of words. Effectively, hackers will run a system which tries random combinations of common words or phrases. Therefore, passwords with common phrases are high risk. Make sure that your passwords are unique so that they are much harder to crack.
- Phishing Scams – The most common type of cyber-attack, phishing scams usually take the form of emails sent to employees. This usually involves an unverified link or document. These links typically contain malware which will infect your system. Clicking on a link or document gives hackers a backdoor entrance to your internal systems and data.
What Makes a Password Strong?
In order to keep your data safe from hackers, it is essential that your employees use strong passwords. Since hackers will often try a series of common words and phrases, passwords should not be overly simple. This means making sure that passwords contain a mixture of upper- and lower-case letters, numbers, and symbols. This will protect you against the two most common types of attacks: brute force and dictionary attacks. Encourage your employees to set longer passwords as these are much harder to crack. Have an internal password policy to ensure that everyone is setting strong passwords.
Take Extra Precautions
Adding an extra step to your security process can save your data. Where possible, use two-factor authentication. Most services offer this as standard, including Google and Microsoft. It works by sending a text to your personal mobile when a new device signs into your account. Two-factor authentication means that even if hackers manage to crack your password, they will not be able to access your private information. Use password managers to avoid data leaks. Password managers allow you to use much stronger passwords without having to remember them. Once you log in to a password manager, you will have access to all of your passwords for your websites and subscriptions. Most password managers will provide suggestions for strong passwords when you sign up to a new website. Google has now built this into their service which helps improve your cyber security.
Step 2: Train Your Staff to Understand Cyber Threats
Train Your Staff to Stop Data Leakage
Your employees are most at risk of giving away sensitive information about your company. Proper training is key to stopping your employees from leaking your data. Ensuring that everyone at your company understands the threats to your cyber security is therefore vital. Make sure to train your employees throughout the year. In particular, make sure your employees are aware of any new cyber threats as they are uncovered. This could include new phishing scams which are one of the biggest threats to the security of your data.
What is a phishing email?
All companies will have to face phishing emails on an almost daily basis. Here are some of the warning signs to look out for:
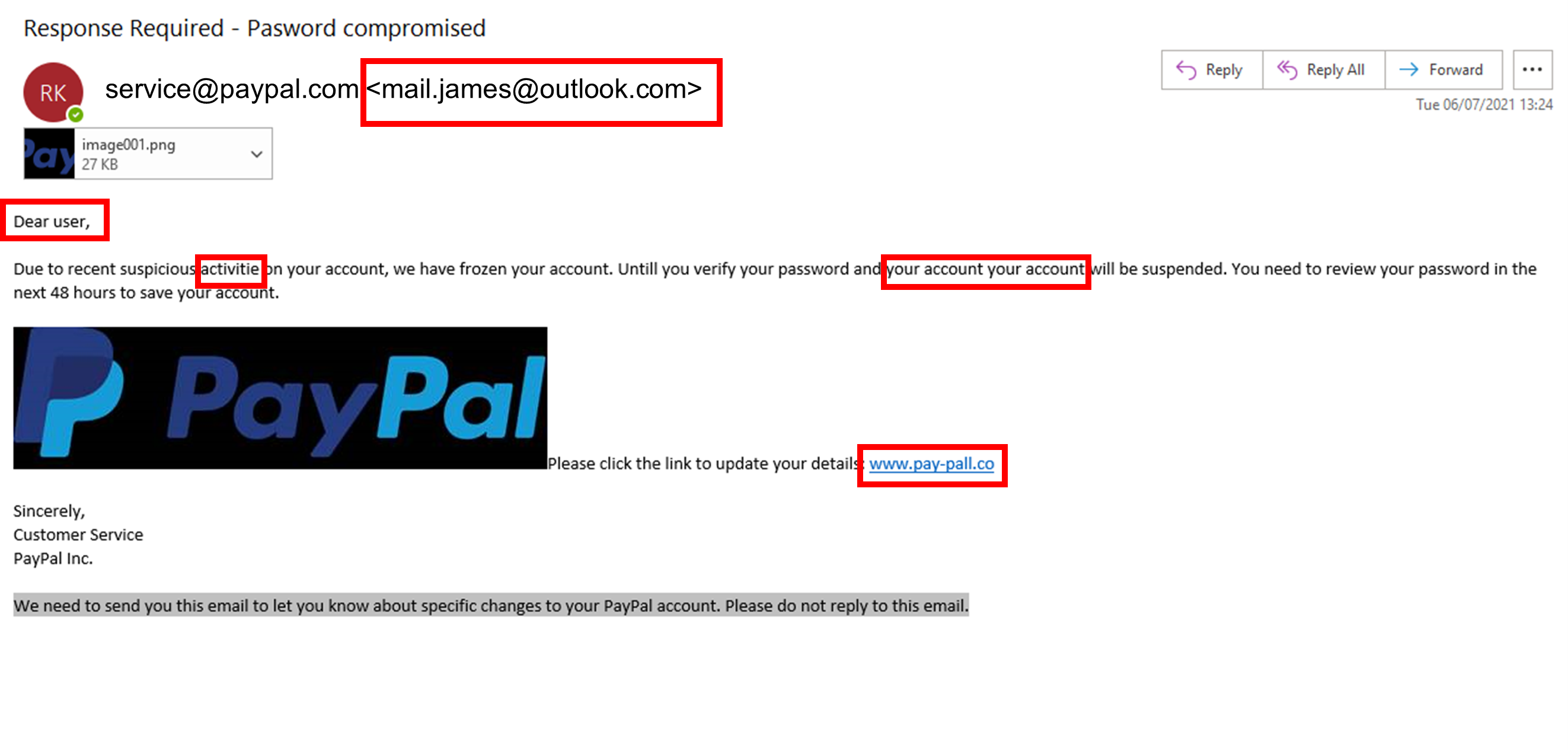
- Abnormal email addresses – Avoid clicking on any links from unfamiliar email domains. If you do not recognize the sender, do not open the link. An unfamiliar email domain is the biggest red flag that you have received a phishing email.
- Spelling and Grammar Mistakes – Be aware of emails that contain typos or poor grammar. If an email seems to come from a reputable company but is littered with these errors, it is likely a phishing email. Additionally, be conscious of the formatting used in the email. If you receive an email that differs from emails you have previously received from a company, report it to your IT manager. Hackers will likely slip up in this area and follow a different style to the company they are impersonating.
- Strange Openers – Most of the time emails will open with a personalized greeting when sent to your private email. For example, most emails will begin “Good Morning Mr Smith” or “Hello John”. Typically, phishing emails will be sent to a large database of people. This means that emails will not be personalized to you. Therefore, if an email begins with a more generic greeting, be wary. Avoid clicking on links in emails that begin “Dear Sir/Madam” unless you recognize and trust the email address.
- Double Check Link URLs – Before you click on a link, check that it comes from a trusted domain. For example, if you receive a link to a company website, make sure that the URL matches the company name. If you are ever in any doubt, do not click on the link.
Anatomy of a Phishing Email
Tip 3: Track and Trace your Data
Keep Information on a Need to Know Basis
As stated before, your people are one of the biggest risks to your cyber security. Therefore, you should restrict access to certain documents and folders on your servers. By restricting access to these files, you ensure that your data does not fall into the wrong hands. This means that your employees cannot gain access to confidential information that does not relate to their job role. This is important as it limits the volume of information available to hackers in the event of a cyber-attack.
Track your Files and Servers
In addition to limiting access to certain files, ensure that you are tracking who accesses each document. This can provide you with insight into any potential data breaches. Using file auditing software allows you to monitor any unusual behavior in your internal systems. In the unfortunate event that you are victim of a cyber-attack, tracking your files can help you figure out which accounts have been breached. This will also help you to determine what information has been compromised.
Back Up your Data Regularly
Ensure that your data is backed up regularly. In the event of a cyber-attack, you will still have vital information that you need to continue with business as usual. Cloud-based solutions are the most efficient solution for this. These allow you to back up your data regularly and efficiently. Backing up your data also helps in the event of a systems failure.
Tip 4: Data Protection While Working from Home
With working from home (WFH) becoming the standard for a lot of organisations, it is important to understand the potential risks that come with this new style of working. Ensuring that you protect the privacy of your employees while they work at home is essential.
Firstly, you should ensure that your employees connect to your servers using a Virtual Private Network (VPN). This makes sure that their connection to the internet is secure. VPNs provide a more secure, encrypted connection for your employees, keeping your data safe. Also, make sure that confidential information is not being shared with other members of the household. Remember, information should be on a need-to-know basis.
Tip 5: Securely Dispose of your End-Of-Life IT
Protection from Cradle to Grave
The previous tips have looked at protecting data on your active IT equipment. However, it is equally important to ensure that your data is erased when you dispose of your IT equipment. Therefore, you must securely erase any traces of your data from your IT equipment at the end of its use. IT Asset Disposal companies, or ITADs, provide these services or you. ITADs will securely erase your data in one of two ways.
Firstly, using government-certified data erasure software known as Blancco, ITADs can securely wipe your data from a hard drive. This software erases every sector of your hard drive to ensure that all of your confidential information is removed.
Secondly, ITADs can shred your Hard Drives. Using government-approved hard drive shredders, ITADs are able to shred your data-bearing assets down to as little as a 6mm shred size. This makes it impossible for anyone to recover data from your old hard drive.
Why is Secure Data Erasure Important?
Although you may be finished with a laptop or PC, others may be interested in gathering the private information stored on them. Therefore, it is essential that all data is erased from a device. If residual data remains on a device, hackers could begin to piece this together. For example, one saved password on a laptop could compromise your entire future IT estate. Therefore, it is vital to your cyber security that you take care of your end-of-life IT assets.
Which ITAD should I use for Data Erasure?
When selecting which ITAD to use, there are several key aspects to consider:
- Accreditation – In order to ensure that your data is in safe hands, you should work with an ITAD which has the proper accreditation. Accreditations provide you with the peace of mind that an ITAD has been audited. This ensures that they are following the proper practices.
- Experience – By working with an ITAD with a long history in the industry, you ensure that your data is being cared for by experts. Firms with more experience in the industry will have more streamlined processes and better security for your data-bearing assets.
- Reporting – You should only trust ITADs which will provide you with a suite of reporting throughout the data erasure process. This provides you with evidence that your data has been erased fully. Without data sanitisation reports, you would not be able to prove that your data has been handled safely.
Re-Tek are one of the most accredited ITADs in the UK and are able to provide a solution to your IT asset disposal needs, no matter how big or small. With 25 years of expertise in the industry, Re-Tek will ensure that your data is handled securely and will provide you with a suite of reporting proving that all services have been carried out properly. To view the range of services Re-Tek offer, click here.







